Security in Mira networks¶
Link-layer security¶
Link-layer encryption means that the packets being sent on the wireless link between nodes in the network are encrypted to protect agains eavesdropping and injection of packets.
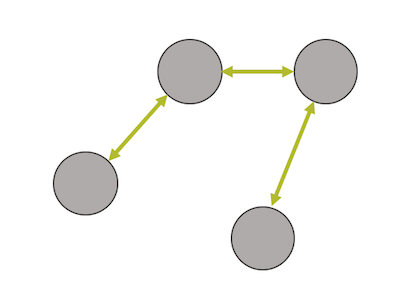
Figure 1: Secure links between nodes.
In Mira networks AES (of at least 128 bits) with CCM mode is used to obtain the link-layer security. This means that only nodes that share the network's AES keys can access the network and the data on the network. AES-CCM provides both encryption and authentication of packets.
Gateway's link security¶
Messages containing sensitive information on the serial port between the host computer and the radio are encrypted and authenticated with ChaCha20-Poly1305 together with unique session keys.
ECDH with curve 25519, HKDF and a 128 bit salt generates the session keys.
The radio generates its private key the first time it boots. The host generats a new, random private key every time it starts.
The host program stores the radio's public key the first time it starts and will refuse to use the radio if the key is changed.
Gateway's firmware root of thrust¶
The serial bootloader on the gateway's radio verifies firmware upgrades with ECDSA with secp256k1 and SHA-256.
The USB bootloader verifies firmware upgrades with ECDSA with secp256r1 and SHA-256.
The firmwares are signed by Lumenradio.
End-to-end security¶
Some applications require additional levels of security. It may be required to ensure data integrity for data going outside of the network onto non-secure data links. Or it may be required to ensure data privacy where the application must prove that intermediate routing nodes can not get access to the data inside the packet. Another case may be where it's required to know that data originated from the correct device, to avoid spoofing.
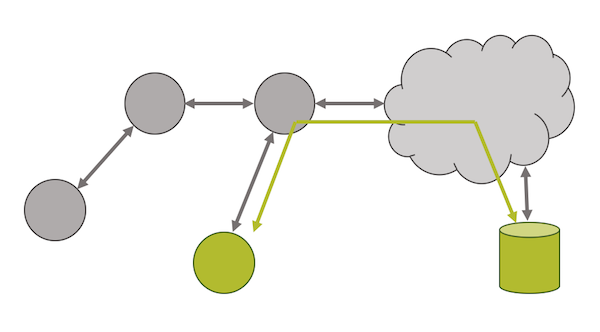
Figure 2: Secure connection between end node and server.
tinyDTLS¶
For applications that require end-to-end security it's recommended to use DTLS or another proven method for data privacy and authentication. Thanks to Mira having IPv6 support, any stack agnostic DTLS implementation should work fine, for instance tinyDTLS that is available in a standalone version from RISE SICS.